In the modern IoT Solutions often we have a big number of devices, connected to the back end: thousands hundred thousands or even millions of devices.
All these devices should have initial configuration and to be successfully connected to the back-end and this configuration should be done automatically.
In a sequence of article there will be described the main concepts of automatic provisioning and best practices how to implement it (focusing more on Azure based IoT solutions).
Challenges:
If devices are configured in advance during the manufacturing it will be:
1. very difficult to know in advance the connection settings during the manufacturing. For big solutions it is possible to know the customer, but it is difficult to know details about exact connection in advance.
2. Setting the connection in advance is not secure. This approach will give options if somebody know the settings to initiate connection from a fake device and to compromise the system.
3. In the modern IoT solutions it is recommended to have implemented MFA (multi factor authentication).
To be possible to have zero touch provisioning is needed to have pre-set of the devices from the back-end.
This initial configuration includes 2 groups of settings:
- Settings, related to the exact connection of the devices to the back-and : end point and authentication
- Settings, related to the specific IoT Solution business logic as logical grouping of the devices, which could be done from the back-end
The first group of settings needs communication between back-end and devices to let them know it’s connection and to provide authentication.
How is possible devices to have automated configuration? The most common approach is to have a common “discovery” service for the whole solution.
This service will not be changed and devices will connect to this service to receive its settings.
To provide MFA for device registration information on manufactured devices with their specific properties should be imported in advance in the system. This import should be based on the information, provided from the device’s manufacturer. It will be not possible somebody non-authenticated from outside to provide this production data import.
Authentication of devices for initial provision should be provided using 2 independent channels (MFA). Usually those c channels are:
- Import of the manufactured device data
- Authentication of devices to establish communication channel, used for provisioning
Authentication of devices to establish connection for initial provisioning can be done in several ways:
- Basic authentication (not recommended)
- Integrated authentication using identity management system like Microsoft Active Directory
- Secure attestation using .X.509 or TPM-based identities
Using authentication with specific credentials brings more complexity and more risk. Most of the modern IoT solutions are designed to use secured connection, based on certificates in different varieties.
The both parts of the authentication are 2 sequential parts of the provisioning process.
- Manufacturing step.
- Solution setup step (back-end setup and device initiated provisioning).
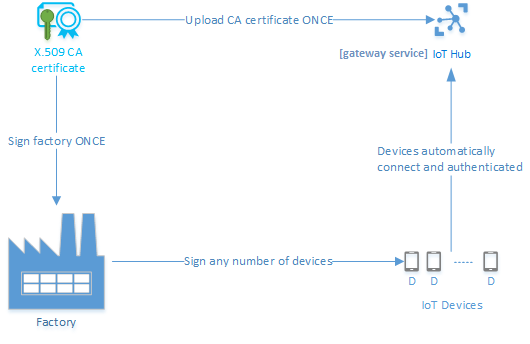
Fig.1 Provisioning based on manufactured devices data and certificates.
Manufacturing step contains:
- Base software install and setup.
- Configuring pre-requisites for device provisioning: global endpoint, certificate etc.
The back-end setup includes:
- Importing information about devices to the back-end system.
- Integration with PKI (importing of public certificates in the IoT Solution) – when certificate based security is implemented
- Integration with identity management system – when authentication is based on this approach.
- Configuring an appropriate discovery service (IoT Hub Device Provisioning Service in Azure), which is able to assist during the provisioning and when device is authenticated to sent the settings to the correct gateway service (IoT Hub).
When the back-end configuration is done it is possible to start the provisioning process, initiated from the device.
Fig.2 describes detailed the common approach for modern zero-touch device provisioning.
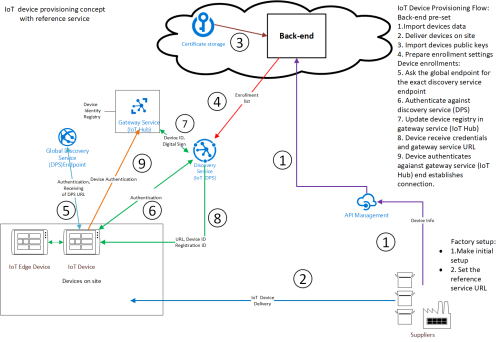
Fig.2 IoT provisioning concept.
